UNAM Darknet
UNAM Darknet (Archive)

Background
Back in 2009-2010, the Intrusion Detection department of UNAM-CERT designed and developed the UNAM Security Telescope, a hybrid of a network telescope and a large-scale honeypot/sinkhole darknet. It featured dynamic public IP assignment, managing approximately 45,000 to 50,000 public IP addresses via NOC routing.
This Security Telescope enabled the collection of valuable data that was transformed into actionable security intelligence used for incident response, monitoring, detection logic development, and malware analysis.
The UNAM Darknet, a core component of the Security Telescope, was refined over subsequent years. It was partially the result of a bachelor’s thesis and graduation project from the Faculty of Engineering at UNAM. The design was documented in the thesis by Javier Santillan, 2011:
- Darknet, motor de detección de tráfico malicioso para el telescopio de seguridad de la UNAM (Local Mirror)
The first version of the UNAM-Darknet was designed in 2009 and implemented at large-scale between 2009-2011. It later served as a reference for data analysis and information exchange within the UNAM network and with external cybersecurity organizations, academic institutions, and The Honeynet Project.
Note: Even though this project is already outdated on its implementation, tools and data analysis techniques, its idea and design are still valid and feasible for new modern implementations using new tools and frameworks for data collection and analysis. In the near future, Honeynet UNAMex Lab will look for potential options to port a modern version o a Darknet-NG to be deployed within the available network IP space of the project.
Overall Design
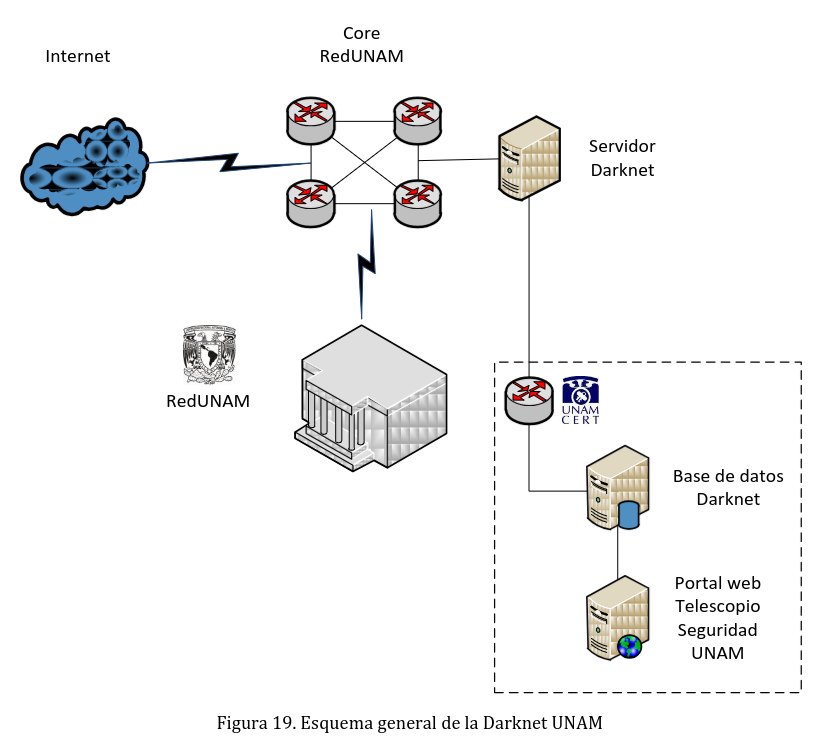
The high-level architecture of the UNAM Security Telescope and UNAM-Darknet is shown below.
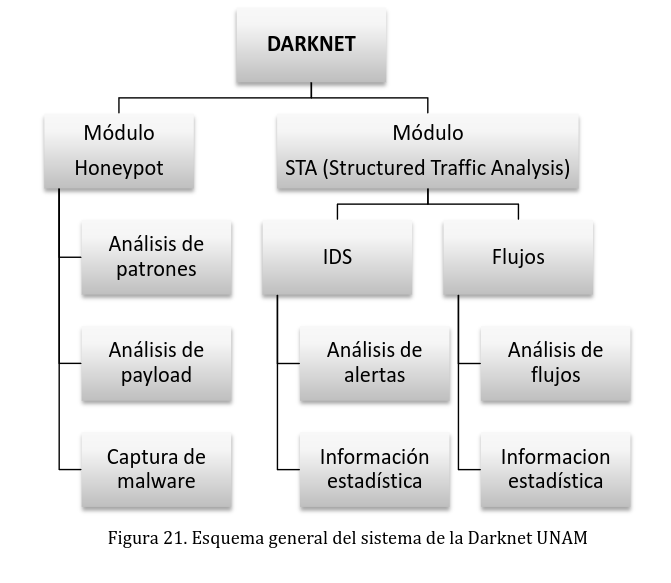
The UNAM-Darknet was designed with the following primary modules:
- Honeypot module
- Network IDS module
- Network flow analysis module
General Capabilities of the Detection Engine
Threat Detection
- Identification of potentially suspicious traffic:
- Scan detection (pattern-based)
- Worm, bot, and virus propagation (signature-based)
- Brute-force attacks
- Targeted attacks using spoofing techniques
- Botnet and P2P network activity detection
Malware Handling
- Malware capture
Automated Network Traffic Analysis
- Structured traffic analysis
- IDS alert correlation
Statistical Information
- Network flow statistics
- Signature-based detection
- Detection of misconfigured devices
Forensics
- Evidence collection and long-term storage
- Payload extraction and analysis
Emerging Threats
- Detection of new and evolving attack trends
Darknet Modules
Honeypot Module
The UNAM Darknet Honeypot module was primarily based on well-known low-interaction honeypots of the time, which were fine-tuned for performance and consistency in data extraction. The main tools included:
Structured Traffic Analysis Module
This module collected, parsed, and analyzed the network traffic captured by the Darknet. A full-packet collector processed the traffic to extract relevant information such as statistics, payloads, and IDS alerts.
Primary tools used:
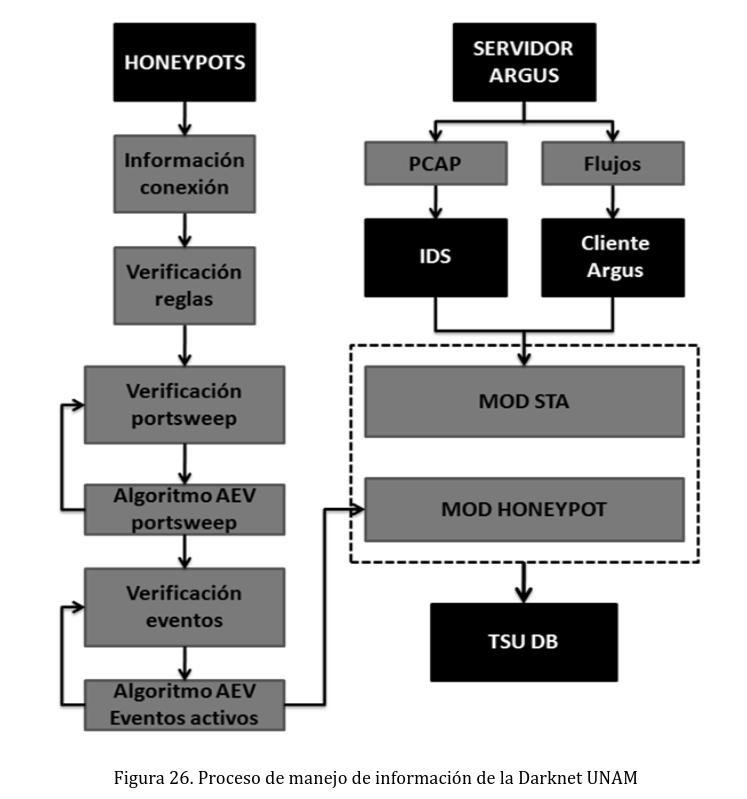
The integration of the Honeypot Module and the Structured Traffic Analysis Module is illustrated in the following diagram:
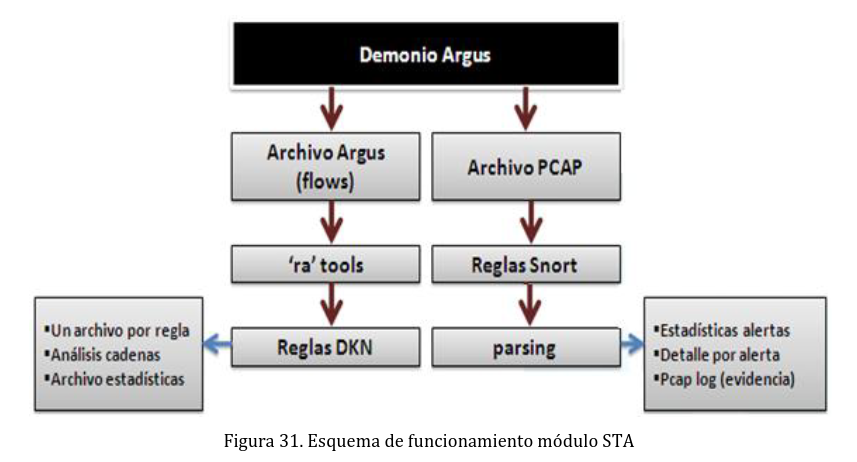
The flow analysis module was implemented as follows:
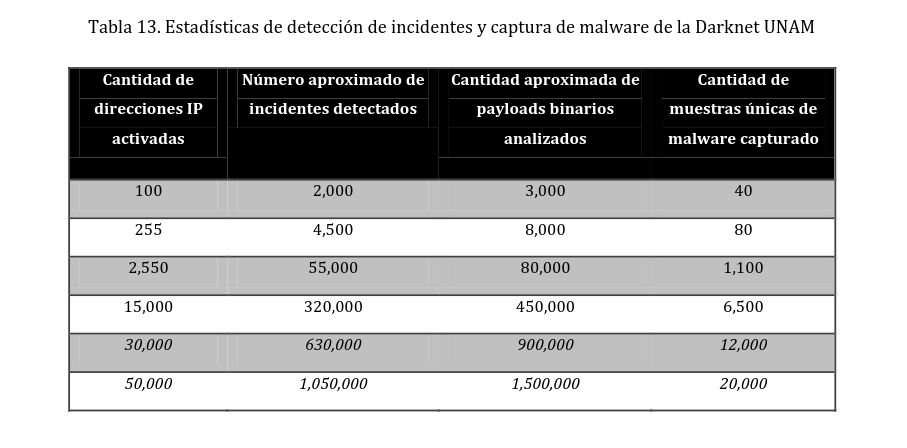
Some of the results of the large-scale data/traffic collection and security intelligence processed:
References and Resources
- Presentation of UNAM Security Telescope during the UNAM DISC (International Day of Computer Security) 2009 :Local-Mirror]
- Presentation of UNAM Security Telescope during the UNAM Computer Security Conference 2010: [Source] [Local-Mirror]